An Overview of Slack eDiscovery
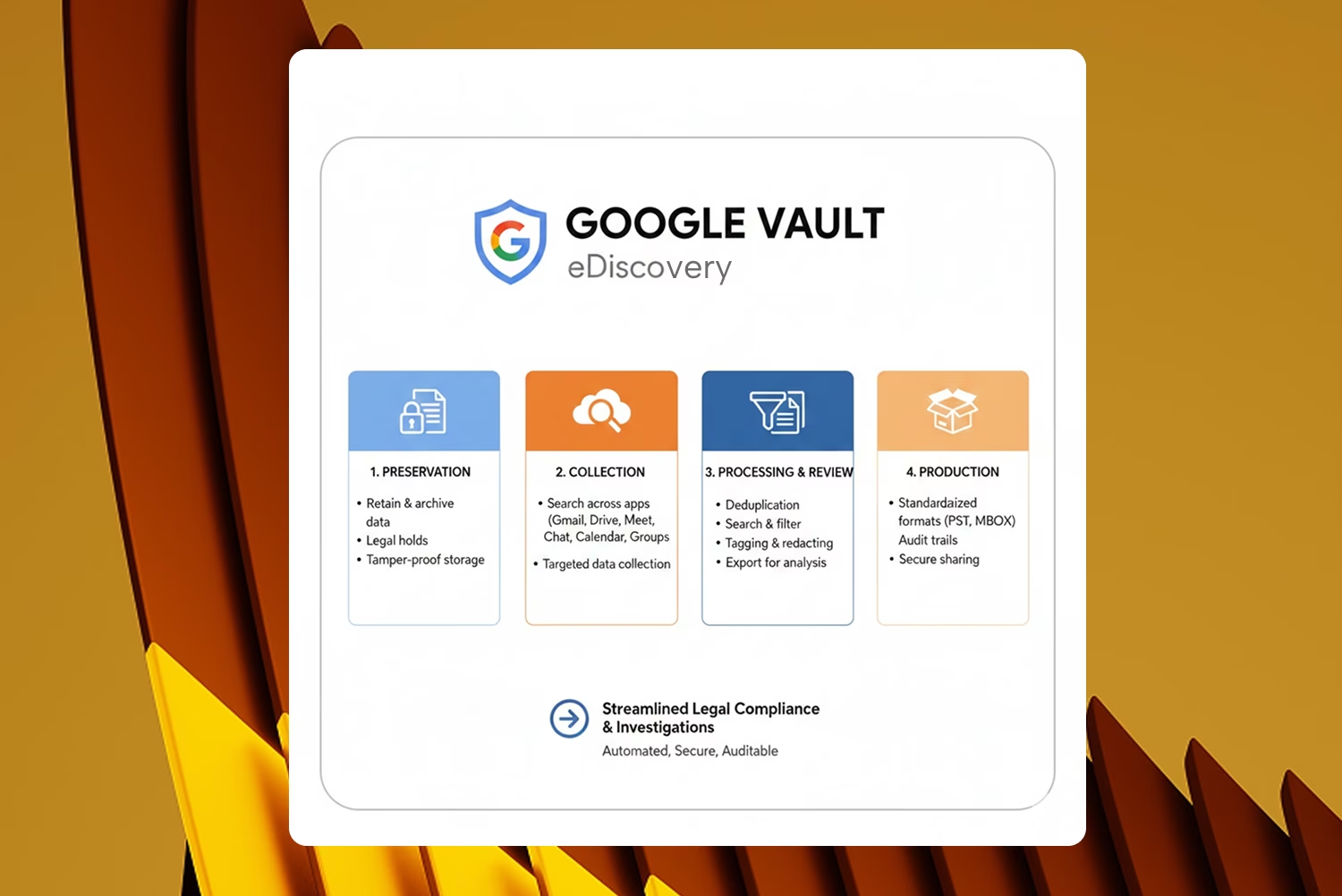
Slack eDiscovery is the process of identifying, preserving, collecting, and reviewing data from Slack workspaces for legal matters, regulatory investigations, internal audits, or compliance requirements.
Organizations use Slack for fast, informal communication, which makes it a critical source of evidence for:
- Employment litigation: Terminations, harassment claims, retaliation cases
- Commercial disputes: Contracts, vendor relationships, deal negotiations
- IP theft cases: Trade secrets, confidential information
- Regulatory investigations: Financial misconduct, data breaches, GDPR/CCPA compliance
Unlike email, Slack data isn't easily searchable or exportable with standard tools. This guide covers:
- Why Slack eDiscovery is critical
- Legal and technical challenges
- How to preserve, collect, and review Slack data
- Best practices for defensibility
Why Slack Matters in eDiscovery
Many organizations assume Slack isn't subject to the same legal holds and discovery obligations as email. This is incorrect.
Courts and regulators increasingly demand Slack data, for several reasons:
1. Business-critical conversations happen in Slack
Slack replaced email for many day-to-day communications. Deal negotiations, HR decisions, and strategy discussions often occur in Slack channels or direct messages (DMs).
2. Informality = high-value evidence
People write more candidly in Slack than in email. This makes it a goldmine for attorneys seeking unfiltered opinions or admissions.
3. Slack data is not automatically preserved
Unlike email, where most organizations use retention policies and archiving, Slack data can be:
- Deleted by users (on some plans)
- Removed via retention policies
- Lost when users are deactivated
If you don't export and preserve Slack data before it's deleted, it's gone forever (and you risk spoliation sanctions).
Legal Obligations for Slack eDiscovery
When Do You Need to Preserve Slack Data?
Under U.S. law (and similar frameworks internationally), you must preserve potentially relevant data once litigation is "reasonably anticipated."
Triggering events include:
- Receipt of a litigation hold notice
- Filing or threat of a lawsuit
- Government subpoena or investigation
- Internal HR investigation (if litigation is likely)
Key principle: If Slack could contain relevant evidence, you must take steps to preserve it. Failing to do so = spoliation (destruction of evidence), which can result in:
- Adverse inference instructions (judge tells jury to assume deleted evidence was bad for your case)
- Monetary sanctions
- Dismissal of claims or defenses
Responding to Subpoenas & Court Orders
When your organization receives a subpoena demanding Slack data, you need to act immediately to preserve data, evaluate objections, and coordinate collection and production within tight deadlines. The typical response timeline is 30-40 days from receipt to production, and preservation must happen on Day 1. Our Slack subpoena response guide covers the complete process, from preservation through production, including objection strategies, cost estimates ($15K-$100K), and common mistakes to avoid.
What Slack Data Is Discoverable?
Generally, all Slack content is subject to discovery if it's relevant and proportional to the case:
- Messages: Public channels, private channels, group DMs, 1:1 DMs
- Files: Documents, images, videos shared in Slack
- Metadata: Timestamps, edits, deletions, reactions, user IDs
- Audit logs: Admin actions, workspace changes (Enterprise Grid only)
Note: Deleted messages may still be recoverable in Slack exports or via the Discovery API (if enabled).
Challenges Unique to Slack eDiscovery
1. JSON Format Exports
Slack's native export is in JSON format, which is:
- Not human-readable
- Not searchable without specialized tools
- Difficult to load into review platforms (Relativity, Everlaw, etc.)
You need software like ViewExport or other eDiscovery tools to convert, search, and review Slack data.
2. Limited Native Search
Slack's in-app search is not suitable for eDiscovery:
- Can't search across private channels you're not in
- Can't search deactivated users' messages
- Can't export search results in a defensible format
3. Data Retention Policies
Slack offers custom retention policies (e.g., auto-delete messages after 90 days). If enabled, data may be permanently deleted before you can preserve it.
Best practice: Disable retention policies (or create exceptions) once litigation is anticipated.
4. Private Channels & DMs
Slack's export options vary by plan:
- Free/Pro/Business+: Standard export includes only public channels
- Enterprise Grid: Discovery API enables export of private channels and DMs (requires Slack approval)
If key conversations happened in private channels or DMs, you may need to upgrade or work with Slack's legal team.
5. Third-Party Integrations
Slack integrates with hundreds of apps (Jira, Google Drive, Salesforce, etc.). Messages containing data from these apps may not export cleanly, and linked files may require separate collection.
Step-by-Step: Slack eDiscovery Workflow
Once litigation is anticipated:
- Identify custodians: Which employees likely have relevant Slack data?
- Notify custodians: Send a legal hold notice instructing them not to delete Slack messages
- Disable retention policies: Prevent auto-deletion in Slack
- Restrict deactivation: Don't delete user accounts until data is preserved
Step 2: Export Slack Data
For Standard Plans (Free/Pro/Business+):
- Go to Slack Workspace Settings → Import/Export Data → Export
- Select date range and channels
- Download ZIP file (contains JSON files)
For Enterprise Grid:
- Use the Discovery API to export private channels and DMs
- Requires legal justification and Slack approval
Third-party tools:
- Tools like ViewExport simplify the export, search, and review process
Step 3: Process and Convert Data
Raw Slack JSON exports are unusable for review. You need to:
- Convert JSON to readable format (HTML, PDF, or load into eDiscovery platform)
- Extract metadata: Timestamps, user IDs, edits, reactions
- Normalize data: Combine messages into threaded conversations
Most eDiscovery platforms (Relativity, Everlaw, Logikcull) support Slack data if properly formatted. Alternatively, use Slack-specific tools.
Step 4: Search and Cull
Search Slack data by:
- Keywords: Names, deal terms, project names
- Date ranges: Narrow to relevant time periods
- Custodians: Filter by specific users
- Channels: Focus on relevant channels (e.g., #legal, #hr)
Tip: Slack's informal nature means people use shorthand, emojis, and slang. Broaden your keyword list accordingly.
Step 5: Review for Privilege and Relevance
Review Slack messages the same way you'd review emails:
- Mark privileged content: Attorney-client communications, work product
- Code for responsiveness: Relevant, not relevant, hot documents
- Redact sensitive info: PII, trade secrets (if producing)
Step 6: Produce to Opposing Counsel
Export responsive Slack messages in the agreed-upon format:
- Native format: JSON (with load file)
- TIFF/PDF: With Bates numbering
- Concordance/Relativity load file: Includes metadata fields
Include a privilege log for withheld messages.
Best Practices for Slack eDiscovery
1. Preserve Early and Often
Don't wait until you receive a subpoena. Preserve Slack data as soon as litigation is reasonably anticipated.
2. Document Your Process
Keep records of:
- When holds were issued
- Who received hold notices
- What data was exported and when
- Search terms and culling decisions
This creates a defensible process if challenged.
3. Don't Rely on Users to Preserve Data
Users forget, ignore hold notices, or don't understand what's at stake. Centrally export and preserve Slack data at the workspace level.
4. Test Your Export Process
Run a test export before litigation. Make sure:
- Exports capture private channels and DMs (if applicable)
- Deleted messages are included
- Metadata is preserved
5. Work with Experts
Slack eDiscovery is complex. Engage:
- Forensic consultants for complex collections
- eDiscovery vendors (like ViewExport) for processing and review
- Legal counsel experienced in ESI and preservation obligations
6. Address Third-Party Integrations
If critical data lives in integrated apps (Google Drive, Jira, etc.), collect that data separately and cross-reference Slack messages.
Common Slack eDiscovery Mistakes
❌ Waiting too long to preserve
Data may be deleted by retention policies or deactivated users before you act.
❌ Assuming Slack isn't discoverable
It is. Treat it like email.
❌ Relying on in-app search for collection
Slack's native search is inadequate for legal holds. Use exports or third-party tools.
❌ Ignoring private channels and DMs
Key evidence often lives in private conversations. Budget for Discovery API access if needed.
❌ Not testing export tools in advance
Some tools don't capture deleted messages or metadata. Test before you need it.
Slack eDiscovery Checklist
- ☐ Issue legal hold notices to custodians
- ☐ Disable Slack retention policies (or create exceptions)
- ☐ Export Slack data (public channels, private channels, DMs as applicable)
- ☐ Convert JSON exports to reviewable format
- ☐ Search and cull for relevant content
- ☐ Review for privilege and responsiveness
- ☐ Produce to opposing counsel with load files
- ☐ Document every step for defensibility
Tools for Slack eDiscovery
Popular options:
- ViewExport: Purpose-built for Slack eDiscovery; fast search, easy export, affordable
- Relativity/Everlaw/Logikcull: Traditional eDiscovery platforms with Slack support
- Hanzo/Smarsh: Continuous Slack archiving for compliance-heavy industries
For most teams, ViewExport is the fastest and most cost-effective solution.
Conclusion
Slack eDiscovery is no longer optional. Courts and regulators expect organizations to preserve and produce Slack data just like email.
Key takeaways:
- Preserve Slack data as soon as litigation is anticipated
- Use proper tools (not Slack's in-app search) for collection
- Budget for Discovery API access if you need private channels/DMs
- Document your process to prove defensibility
Need help with Slack eDiscovery? Contact us or start a free trial.