Picture this: HR gets a complaint about harassment, or an exec is alerted to a trade leak involving Gmail and Google Drive. Legal is looped in, and leadership needs answers, fast. But the conversations, documents, and decisions you need to review are scattered across Gmail, Google Chat, shared Drive folders, and Slack. That’s where eDiscovery comes in. It’s the process of finding, preserving, and producing electronic records for legal or HR matters.
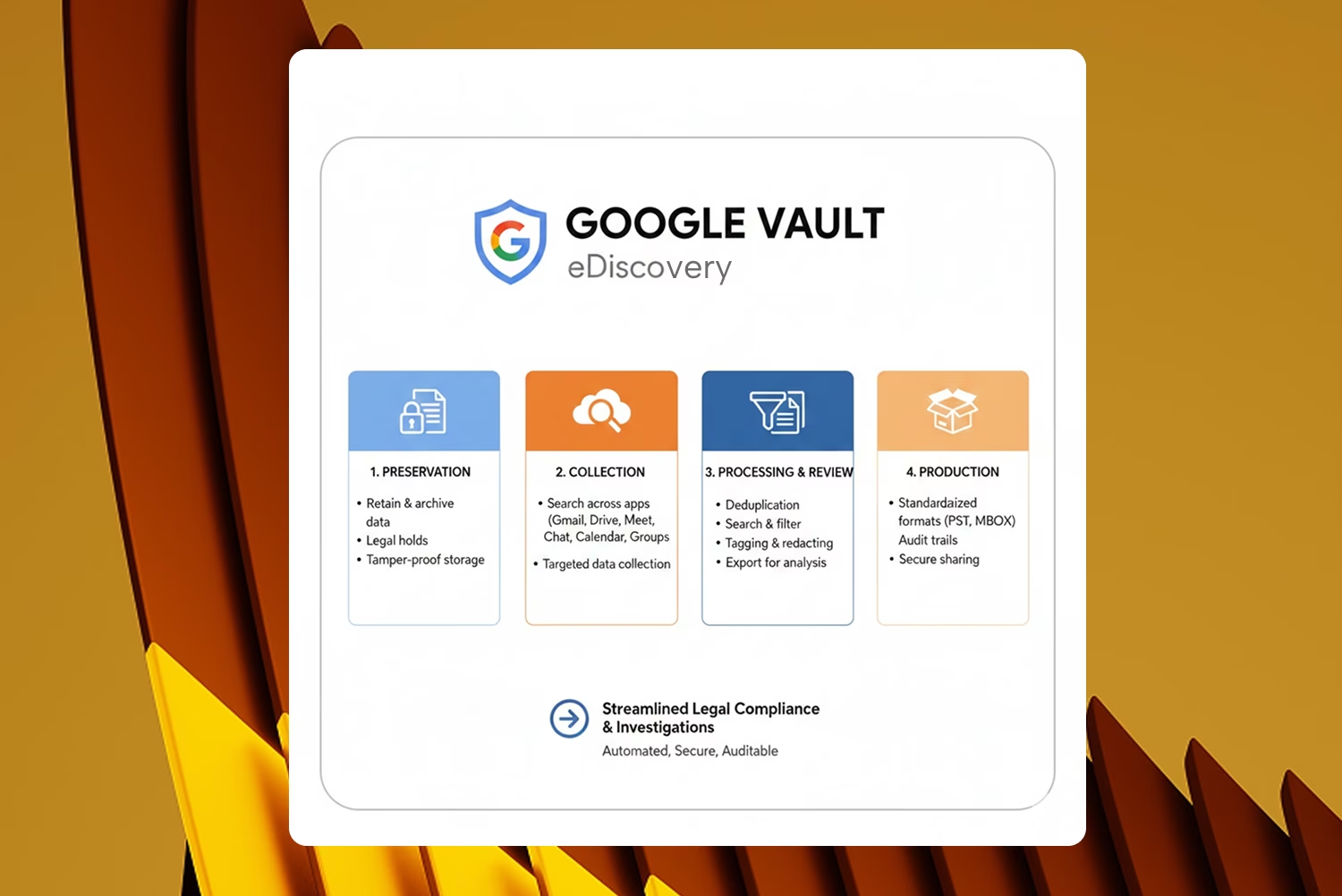
When people say “Google eDiscovery,” they’re usually talking about pulling this off inside Google Workspace using Google Vault – the tool that lets IT and legal teams search, place holds, and export data
This Google eDiscovery guide breaks down everything you know about handling those scenarios, and what to do when your Google data search intersects with other platforms, like Slack.
How Google eDiscovery Works in Google Workspace
Before we get into the meat of this Google eDiscovery guide, here are the key concepts you need to understand.
Core Building Blocks
- Google Vault is the backbone of Google Workspace eDiscovery. While there are plenty of software options in the $14 billion+ eDiscovery market, Vault is the Google-native tool where IT, legal, and HR teams can search, preserve, and export user data. It touches Gmail, Google Drive/Shared Drives, Google Chat messages, Groups, and Meet recordings/transcripts (depending on settings).
- For most organizations, Vault effectively serves as their Google Workspace eDiscovery layer – powering Gmail eDiscovery, Google Drive eDiscovery, and Google Chat eDiscovery from a single place.
- Retention rules define how long data is kept. Organizations use them to meet regulatory requirements or to prevent automatic deletion when an investigation is active.
- Legal holds preserve data from deletion.
- Search lets you target specific users, date ranges, keywords, file types, and content sources.
- Export: Once you’ve identified what you need, Vault exports email in MBOX or PST, and Drive files in their native formats with metadata
- Audit logs / access controls: Every action in Vault – searches, holds, exports – is recorded. Admins can review who accessed what, when, and why. Access is also role-based, reducing risk.
Typical Workflow Using Google Vault
Google eDiscovery typically follows a sequence that looks like this:
- Identify custodians: Start by determining whose data you need to review, including users, groups, and shared drives.
- Run targeted searches: Vault lets you search across Gmail messages, files in Drive/Shared Drives, and Google Chat messages.
- Apply legal holds: If the matter is active or reasonably anticipated, apply holds to preserve data.
- Export in a defensible format: Once you’ve narrowed the dataset, export the results for downstream review. Exports might go to eDiscovery platforms, opposing counsel, or regulators/auditors. Each export is logged, which helps maintain a clear paper trail.
When Legal and HR Teams Rely on Google Data
Legal, HR, and compliance teams turn to Google Vault when they need fast, defensible access to Workspace data.
Common Use Cases
Matters involving performance concerns, harassment claims, or allegations of discrimination often require reviewing Gmail threads, Chat conversations, and shared documents to understand what was communicated and when.
- IP and trade secret leaks:
If confidential info is leaked – a confidential slide deck emailed to a personal account, a Drive link shared outside the organization, or unusual file access around a product launch.
- Regulatory investigations and audits:
Regulators may require proof that records were preserved, retained, or produced correctly.
- Internal policy violations:
Cases involving misuse of company tools, inappropriate content, or conflicts of interest.
The data involved in the eDiscovery process is central to case outcomes – the EEOC recovers more than $660 million annually for workers in cases involving discrimination
What Makes Google eDiscovery Different from Email-Only Tools
Google eDiscovery requires you to go beyond email threads to incorporate a blend of data. This changes how searches work.
- There’s a mix of structured data (email headers, metadata) and unstructured content (docs, slides, sheets).
- Collaboration features such as comments in Docs/Sheets/Slides can introduce important context (as can Shared Drives with many contributors).
With Google Workspace, you’re rarely reviewing a single standalone file. To paint the full picture, you need to understand the context around a document.
Limits of a Google-Only eDiscovery Strategy
This is an important part of our Google eDiscovery guide: limits. When your feet are to the eDiscovery fire, a Google-only search might seem like it checks all of the boxes. But the reality is you’re likely to miss critical conversations happening elsewhere, especially in places like Slack, which is home to more than 40 million daily active users.
Here’s why your search needs to span beyond Google.
Communication Has Moved Beyond Email
The way teams communicate has shifted. They now use Slack for day-to-day conversation, and Google Workspace for docs and email.
Because of that split, many sensitive conversations never actually touch Gmail or Google Chat at all. For example, early-stage fundraising or pre-IPO talk can happen in Slack channels, while informal HR-related messages can be shared through private Slack DMs.
Legal Risk: Blind Spots Outside Google Workspace
A Google-only approach creates gaps, which can not only throttle your eDiscovery efforts, but also open you up to significant legal risk. Key evidence often lives in Slack channels and DMs, where key decisions or misconduct happen. It can also appear inside conversations that don’t show in Gmail/Drive eDiscovery, but still matter to a case.
For example, a manager might discuss firing an employee in a private Slack channel (instead of email), while engineers share source snippets or sensitive design decisions in Slack. If those conversations matter to the case and you can’t surface them, your search is incomplete
Where Slack Fits into Your Google eDiscovery Process
Google Vault covers a wide swath of eDiscovery data, but most orgs don’t operate exclusively inside Google tools. If you use Slack, you’ll need to expand your search efforts.
How Slack Data Is Typically Retrieved
Exporting Slack conversations depends on your workspace plan and permissions (Workspace Owners/Admins, Org Owners/Admins can export data). In the Free plan, you can export the basics, like messages and file links. In the Business+ plan, you can export from public & private channels, as well as DMs. Enterprise takes things a step further and allows for exports by conversation type and by single user.
The end result: a tangled web of JSON files for thousands or millions of messages across channels and DMs. nested into folders, which is nearly impossible to filter through, and which lack any formal audit trail. To an IT Director or attorney, that nightmare export is basically unreadable without the use of another tool.
Best Practices for a Defensible Google + Slack eDiscovery Workflow
A defensible eDiscovery workflow requires a clear structure that spans both Google Workspace and Slack, so your team can easily collect, preserve, and produce key data.
Step 1 – Map Where Your Data Actually Lives
Start by identifying the primary systems your org uses. This might include Google Workspace (Gmail, Drive, Chat), Slack (public channels, private channels, DMs), and other sources like HR or ticketing software.
Create a simple data inventory so Legal knows where to look when something happens.
Step 2 – Standardize Legal Hold and Retention Policies
Google Workspace and Slack don’t always align out of the box. Standardizing your retention policies across Google Workspace and Slack as much as possible reduces the chance of accidental data loss.
Step 3 – Use the Right Tool for Each System
For Google Workspace data, you’ll use Google Vault to search, hold, and export data. However, you should use a Slack export viewer or Slack JSON viewer to:
- Make sense of Slack exports.
- Keep a clear audit trail of who searched what.
- Avoid direct manipulation of raw JSON files.
Step 4 – Keep the Chain of Custody Clean
Clearly document the following to create a defensible, traceable workflow:
- Who requested the data
- Who accessed and searched it
- When exports were created and shared.
Ensure that any exports into platforms like Relativity, Everlaw, or Logikcull are also documented & consistent with internal policies.
What to Look for in a Slack eDiscovery Tool (to Complement Google)
Once you have Google Vault dialed in, the next challenge is ironing out your Slack eDiscovery flow. Here’s how to find a tool that makes Slack’s dizzying JSON exports usable, reviewable, and defensible.
Core Capabilities
A Slack eDiscovery tool needs to bridge the gap between Slack’s raw JSONs and a structured review experience. It should be able to:
- Upload and parse Slack exports (ZIP/JSON).
- Present the data in a readable, conversation-style view.
- Filter by: workspace/member, channel vs. DM, date/time range, keywords/phrases.
- Support for exporting in formats legal teams already use, like CSV, or formats ingestible by major eDiscovery platforms.
Legal and Compliance Requirements
Beyond usability, a Slack eDiscovery tool must stand up to legal scrutiny.
- Audit trail
Search history, user actions, and export logs tied to specific users, creating a clear record of how data was accessed and handled. - Role-based access
Limit who can see sensitive channels or DMs, ensuring only authorized personnel interact with protected data. - Defensibility
Defensibility typically requires consistent processes that can be described to a court or regulator. - Security
Clear policies around how Slack data is stored, encrypted, accessed, and monitored.
A strong Slack eDiscovery tool should also support your Slack compliance obligations by respecting retention settings, legal holds, and audit requirements across matters.
How ViewExport Fits into a Google-Centric eDiscovery Stack
If Google Vault is already part of your eDiscovery system, and you’re looking for a Slack-suitable counterpart, solutions like ViewExport are what you need.
Typical Scenario
Here’s what happens: a lawsuit, HR complaint, or regulator inquiry hits. Your legal/IT team uses Google Vault to quickly pull Gmail/Drive/Chat data, and they request a Slack export from an admin.
Now, they have clean Google Workspace data from Vault, and a messy Slack export ZIP that no one wants to touch.
Here’s how ViewExport solves your problems:
Using ViewExport Step-by-Step
- Step 1: Upload the Slack export ZIP to ViewExport.
- Step 2: Use ViewExport to search and filter messages by custodian, channel, time window, and keywords. You can also narrow down to messages that matter for the matter at hand.
- Step 3: Export the result to CSV or other formats for:
- Ingestion by an eDiscovery platform (Relativity, Everlaw, etc.).
- Sharing with outside counsel or opposing counsel.
- Step 4: Maintain defensibility by relying on ViewExport’s logs/audit trail instead of manual JSON wrangling. You’ll also have a clear, repeatable process for how Slack data was handled.
ViewExport for Different Teams
ViewExport is right for you if you’re:
- Corporate IT and in-house legal
ViewExport helps internal teams move quickly when a subpoena or internal investigation lands on their desk. IT no longer needs to lean on engineering to interpret Slack’s JSONs, and legal can review conversations in a format that feels familiar and actionable
- Law firms and eDiscovery service providers
For firms supporting multiple clients, ViewExport is a straightforward way to add Slack data to your existing Google-focused workflows. Instead of reinventing the process for each matter, you can create a consistent method for handling Slack data.
Implementation Checklist: Bringing Google and Slack Under One eDiscovery Umbrella
Unifying your Slack & Google eDiscovery efforts is simple. Here’s a quick checklist you can use to tighten your processes:
- Confirm Google Vault is configured correctly for all relevant data types, like Gmail, Drive/Shared Drives, Chat, Groups, and Meet content.
- Review data retention policies and legal hold procedures across Google Workspace and Slack, to ensure they don’t conflict.
- Document where high-risk conversations usually happen, like Gmail, specific Slack channels and DMs, Google Chat spaces, or other systems.
- Select a Slack export tool or Slack eDiscovery/search tool and test it with a sample export to confirm it makes the JSONs user-friendly and supports fast Slack archive search.
- Run a mock investigation that pulls from Google data (Vault) and Slack data (via your Slack eDiscovery tool), to test your joint process under “pressure.”
- Document your end-to-end workflow – searches, holds, exports, and chain-of-custody steps – so the process is repeatable for future matters.
Make Sure Your eDiscovery Covers More Than Google
Google Workspace and Google Vault give you strong building blocks for eDiscovery. But real-world matters rarely stay inside a single system, and often surface in Slack.
A reliable way to bring Slack into the same structured workflow as Google is essential. That means being able to parse exports, search conversations, preserve context, and produce results with the same confidence you have in Vault.
Review how you handle Slack exports today and test a tool like ViewExport with a sample archive to see how well it fits alongside your current Google eDiscovery and eDiscovery platforms.